Use CloudFlare with ServerPilot
Cloudflare is a popular content delivery network (CDN) that provides many features including a Web Application Firewall (WAF).
ServerPilot configures your server to understand the
X-Forwarded-For headers used by Cloudflare
and to trust X-Forwarded-For headers from Cloudflare’s IP addresses.
Your log files will show the real client addresses,
not the Cloudflare proxy addresses.
For domains using Cloudflare:
- The SSL certificate seen by web browsers will be the certificate provided by Cloudflare.
- The app’s SSL certificate will only be used to secure traffic between Cloudflare and your server.
Configure Cloudflare for AutoSSL
To prevent Cloudflare’s WAF from blocking AutoSSL domain authorization requests, perform the following for each domain.
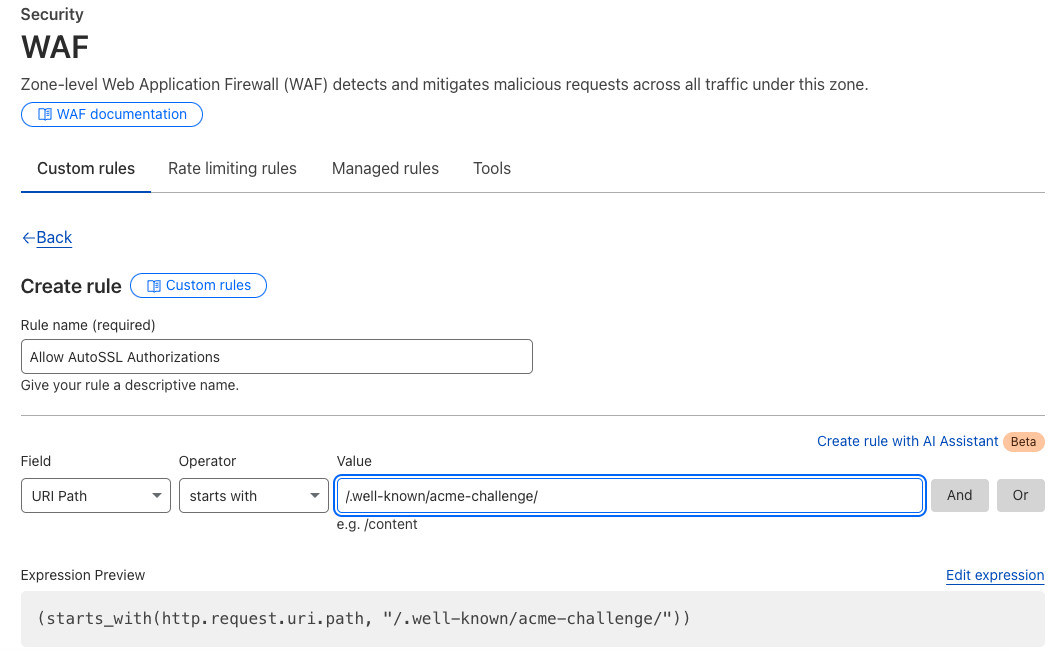
- In Cloudflare, navigate to Security > WAF > Custom rules.
- Click Create rule.
- Set Rule name to “Allow AutoSSL authorizations”.
- For Field, select URI Path.
- For Operator, select Starts with.
- Set Value to:
/.well-known/acme-challenge/
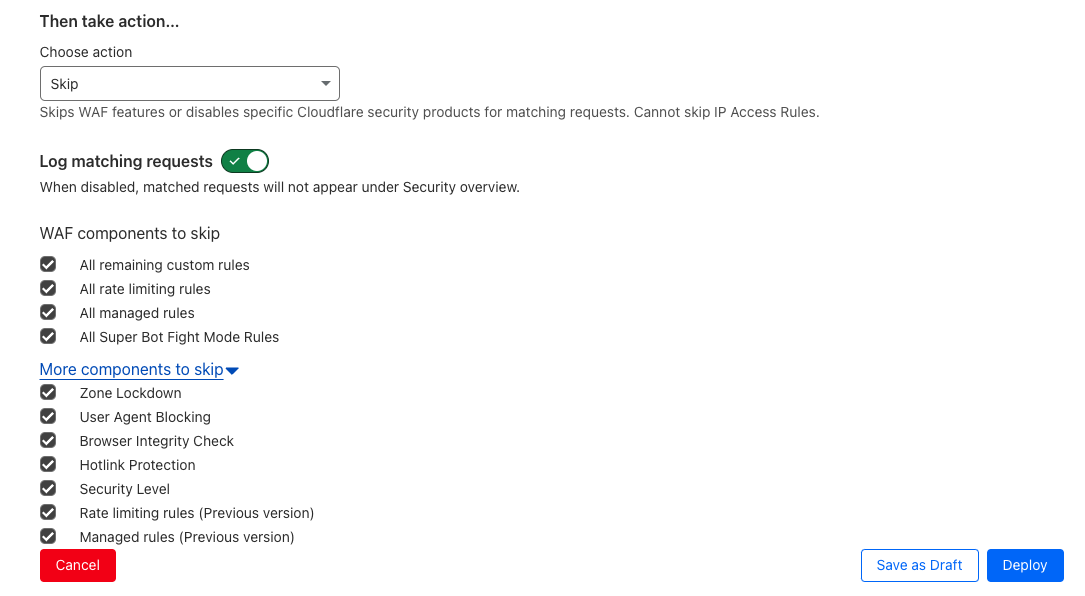
- For Then take action…, select Skip.
- For WAF components to skip and More components to skip, select all components.
- For Place at, select First.
- Click Deploy.
Cloudflare Origin CA
If all domains of an app are using Cloudflare, clients such as browsers will only see the SSL certificate issued by Cloudflare. In this case, rather than AutoSSL, your app can use a custom SSL certificate issued by the Cloudflare Origin CA. Certificates issued by the Cloudflare Origin CA are trusted by Cloudflare and are valid for up to 15 years.