Generate an SSL key and CSR
Before a Certificate Authority (CA) can issue a signed SSL certificate, you must provide the CA a Certificate Signing Request (CSR). The CSR specifies the domain names to be included in the certificate along with information about the organization the certificate will belong to.
A new private key is often generated at the same time as generating a CSR. The certificate you will later receive from the CA will only work with the same private key you used to generate the CSR.
There are two ways to generate an SSL private key and CSR: either using ServerPilot or manually through the command line.
Generate a key and CSR using ServerPilot
Using ServerPilot is the easiest way to create a key and CSR.
First, go to your app’s SSL tab in ServerPilot.
Next, enter your app’s domain followed by your location and organization name. Click on Generate Key and CSR.
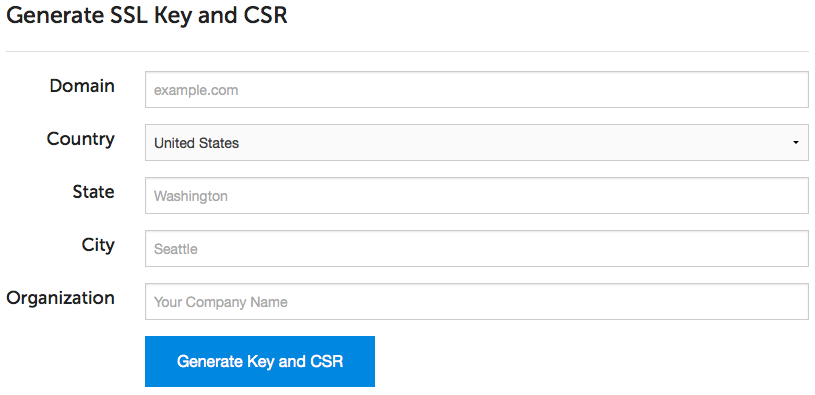
ServerPilot will automatically generate a CSR and SSL key for your app.
Generate a key and CSR manually
To generate a key and CSR from the command line, you can either:
- provide CSR information through command prompts, or
- provide CSR information through a configuration file.
Provide CSR info through command prompts
To specify the CSR information through command prompts, SSH into your server as any system user. You do not need to be root.
Run the following commands on your server to generate a key and CSR.
mkdir -p ~/certs/YOUR_DOMAIN_NAMEcd ~/certs/YOUR_DOMAIN_NAME(umask 077 && touch ssl.key)openssl req -new -newkey RSA:2048 -nodes -keyout ssl.key -out ssl.csrYou will be prompted to answer a few questions. There are two questions that are critical to answer correctly:
- Common name: Your domain name. For example,
foo.com. Nowadays, you generally should not enterwww.as your Certificate Authority should make the certificate work both withwwwand without. However, you should check with your Certificate Authority to find out. - Password: Do not enter a password or challenge phrase. Just hit enter when you’re asked for a password.
When done, you will have a directory called certs/YOUR_DOMAIN_NAME in
your current system user’s home directory that contains two files:
- ssl.key—This file contains your SSL private key. Don’t lose it!
- ssl.csr—This file contains your Certificate Signing Request.
Provide CSR info through a configuration file
To generate a CSR for a certificate that will include multiple domains or multiple wildcard domains, you will need to generate the CSR using a configuration file.
First, SSH into your server as any system user. You do not need to be root.
Create a file named server.cnf with the following contents.
[req]distinguished_name = req_distinguished_namereq_extensions = req_extprompt = no
[req_distinguished_name]C = USST = StateNameL = CityNameO = OrgNameCN = *.first-domain.example.com
[req_ext]subjectAltName = @alt_names
[alt_names]DNS.1 = *.first-domain.example.comDNS.2 = *.second-domain.example.comReplace StateName, CityName, OrgName, and domain values with the values you need.
Next, run the following command to generate a private key and the CSR.
openssl req -newkey rsa:2048 -nodes \ -config server.cnf \ -keyout server.key \ -out server.csrYour CSR will be in the file server.csr.
Your private key will be in the file server.key.